Visual Traceroute
Why perform a traceroute?
The objective of a graphical traceroute is to discover each server relaying your IP packet from point to another, and to measure the return-trip delay between the probing host (here G Suite.Tools) and each relay on the packet path.
G Suite.Tools' visual traceroute online app makes it easy to precisely pinpoint weak nodes impacting your global network performance. In addition to determining the response time of each hop the packet is travelling through, you're now able to visualize in full screen the path of each probe ping between our server and the tested IP address within Google Maps in a instant.
By tracing the actual route between G Suite.Tools' server and yours, you can decide in which way to optimize your network setup to lower response times in your application, service or website.
Quick How-To
Less is more. Insert the complete (sub.)domain, IPv4 or v6 to which you want to perform a visual traceroute test and press 'TRACE'.
The traceroute tool will then send from 1 to 30 IP packets to the target, incrementing the Time-To-Live (TTL) for each probe ping, starting from TTL 1. In this networking context, the TTL defines the maximum number of hops a packet can be relayed through during its travel over the Internet. Thus, each probe will incrementally reach one relay further than the previous ping. When a packet reaches a network node and gets its TTL credit down to 0, it will stop there and elicit a TIME_EXCEEDED response to be sent back to the ping's origin (G Suite.Tools). That's how our tool can measure the response time of each node within the path of an IP packet.
Results
When getting the traceroute results, feel welcome to enlarge the Google Maps by clicking the fullscreen icon in the top-right corner of the tool.
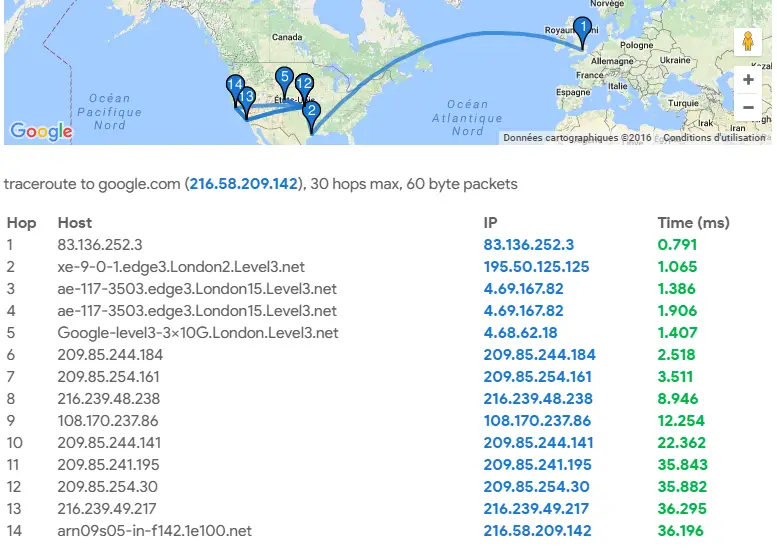
You're now able to deep dive in Google Maps the path of a IP packet from our server to any Internet-connected device.
The table under the map gives you synthetic results over each hop of the tested route. The maximum hops number is limited to 30. Whenever it's possible, we determine the hostname related to each hop we discover. The blue-colored value confirms the IP of each relaying node. We colored in green their return-trip response time (in ms).
Regularly, it's possible that a node is actually configured not to send any TIME_EXCEEDED packet back to the origin. In those case, those node can only relay the packet but won't answer any information related to their network identity. For those hops, we fill in the table line by symbolic asterisks '*' and the map cannot be completed at 100% by lack of information. This is totally expected in most cases if it happens in the middle of the route.
However, if you notice delays or time outs at the very end of the traceroute, there's a chance that something's wrong with one of your infrastructure nodes as those hops are the last one before reaching your target. In that case, I advise you to check if:
- Your local network's firewall is blocking ICMP packets. If it's already accepting HTTP (TCP/UDP) packets, it may not be a real issue, depending on your needs.
- Your local network is correctly connected to Internet. Double check any faulty cable, network card or software on the way.
- There is no declared route back to G Suite.Tools' server. The remote host should get its default gateway and routing tables updated if needed.
- The return-trip takes more than 2 s to reach back our server. The path may be congested and you may upgrade your connection after analyzing it precisly.
Advanced information
This tool is based on Linux open-source utilities traceroute.
This graphical traceroute implementation is set up to track the path of an IP packet to a maximum of 30 hops. These raw ICMP echoes are in the form of ECHO_REQUEST datagrams, eliciting an ICMP TIME_EXCEEDED response from the last hop on the complete trip of a probing packet. The program will wait no more than 2 s before timing out waiting for such TIME_EXCEEDED response packets.
As UDP and TCP-type packets are more commonly blocked or throttled by modern devices or routers, this ping test provides a maximum guaranteed network penetration by using the ICMP protocol.
Tips
- Perform a complete ping test to send 6 probes in a row to a specific hop and get a more focused and consistent report.